What kind of encryption protocols are used to secure the AV solution?
With the increasing number of cyberattacks on businesses and individuals, it is more important than ever to have a reliable and secure antivirus (AV) solution in place. One critical aspect of any AV solution is the encryption protocol used to protect the data it processes and stores. In this article, we will explore the different types of encryption protocols commonly used in AV solutions and their effectiveness in securing your data.
Table of Contents

Introduction to Encryption Protocols in AV Solutions
Encryption protocols are mathematical algorithms used to encode and decode data to protect it from unauthorized access. In AV solutions, encryption is used to secure sensitive data such as user credentials, virus definitions, and updates. Encryption protocols ensure that the data transmitted between the AV solution and other systems is secure and cannot be accessed by unauthorized individuals.
Symmetric Encryption
Symmetric encryption is the most commonly used encryption protocol in AV solutions. It uses the same key to encrypt and decrypt the data, making it fast and efficient. However, it also means that if the key is compromised, all the encrypted data can be easily accessed.
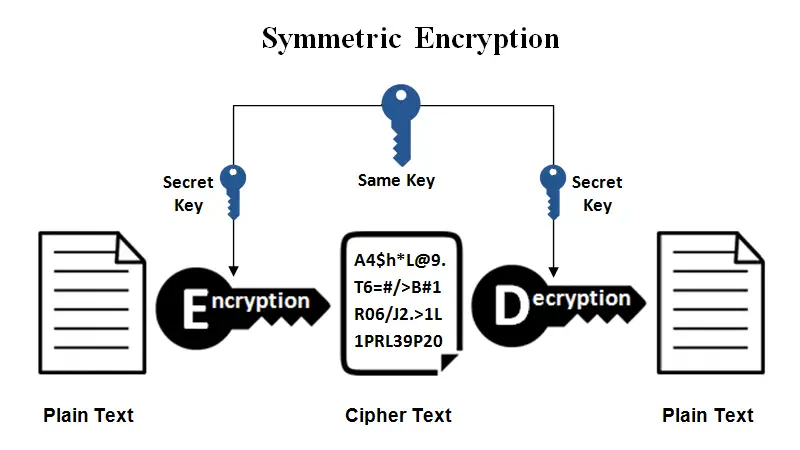
Asymmetric Encryption
Asymmetric encryption uses two different keys, one to encrypt the data and the other to decrypt it. The encryption key is public, while the decryption key is private, making it more secure than symmetric encryption. Asymmetric encryption is commonly used in digital signatures, where the private key is used to sign the data and the public key is used to verify the signature.
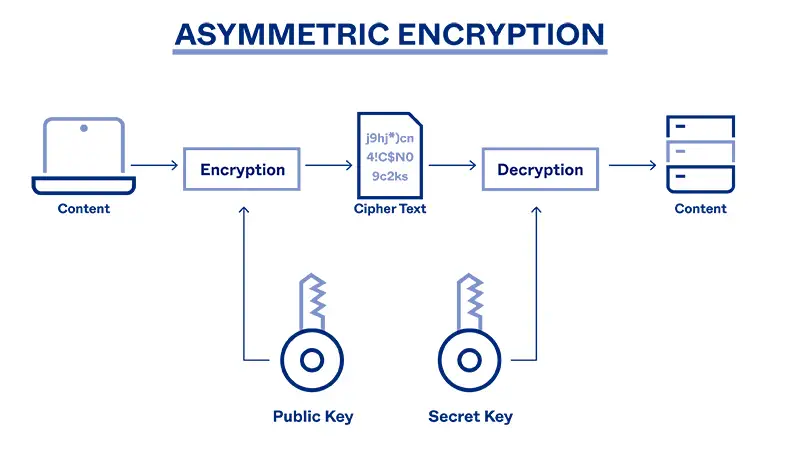
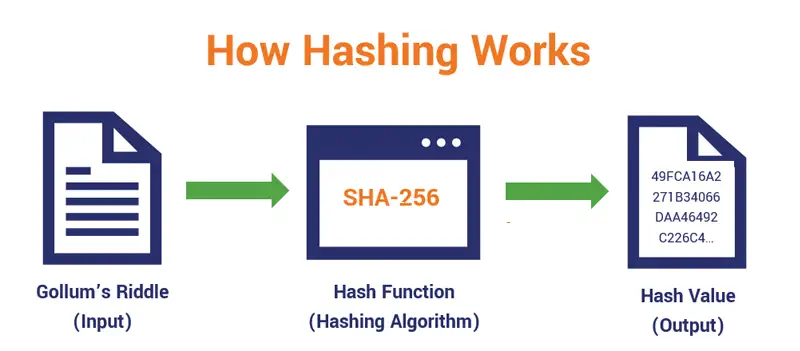
Hashing
Hashing is a one-way encryption protocol used to secure data by converting it into a fixed-length string of characters. Hashing is commonly used to store user passwords in AV solutions. When a user creates a password, it is hashed and stored in the AV solution’s database. When the user logs in, the password they enter is hashed and compared to the stored hash.
SSL/TLS Encryption
Secure Socket Layer (SSL) and Transport Layer Security (TLS) are encryption protocols commonly used to secure data transmitted over the internet. SSL and TLS use asymmetric encryption to establish a secure connection between the client and the server. SSL and TLS are commonly used in AV solutions to secure updates and virus definitions.
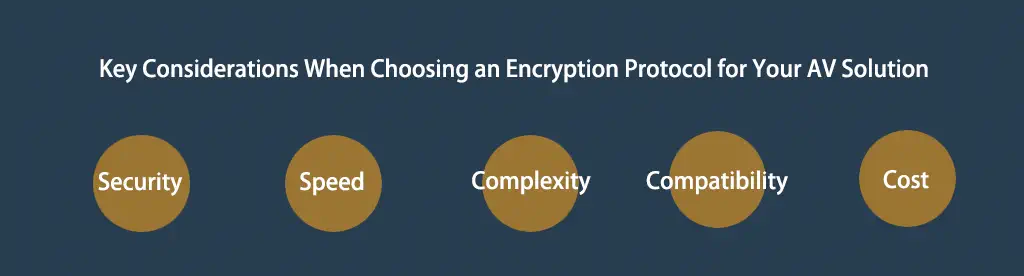
Key Considerations When Choosing an Encryption Protocol for Your AV Solution
-
Security
The primary consideration when choosing an encryption protocol is security. You want to ensure that the protocol you choose is strong enough to protect your sensitive data from unauthorized access. -
Speed
Another important consideration is speed. Encryption can slow down the AV solution, especially if the encryption algorithm is complex. Therefore, it is important to choose an encryption protocol that is fast and efficient. -
Complexity
The complexity of the encryption protocol is another consideration. Some encryption protocols are more complex than others, making them more difficult to implement and manage. -
Compatibility
Compatibility is another important consideration when choosing an encryption protocol. You want to ensure that the protocol you choose is compatible with your existing systems and devices. -
Cost
Finally, cost is a consideration. Some encryption protocols are more expensive than others, and you want to ensure that the one you choose fits within your budget.
Best Practices for Implementing Encryption in Your AV Solution
-
Choose the Right Encryption Protocol
Choose an encryption protocol that is strong enough to protect your sensitive data, but also fast, efficient, and compatible with your existing systems. -
Use Two-Factor Authentication
Two-factor authentication provides an extra layer of security by requiring users to provide two forms of identification, such as a password and a security token. -
Implement Regular Updates
Regular updates to your AV solution and encryption protocols are essential to ensure that they are up-to-date and able to protect against new threats. -
Train Your Employees
Train your employees on the importance of encryption and how to use it effectively. This can help prevent accidental data breaches and ensure that your AV solution is used correctly. -
Monitor Your Systems
Regularly monitor your AV solution and encryption protocols to ensure that they are working correctly and that there are no vulnerabilities that could be exploited by hackers.
Conclusion
Encryption protocols play a crucial role in securing AV solutions. Symmetric encryption is fast and efficient, but not as secure as asymmetric encryption. Asymmetric encryption is more secure, but slower and more complex. Hashing is used to store passwords securely, while SSL/TLS encryption is used to secure data transmitted over the internet. Understanding the different types of encryption protocols used in AV solutions can help you choose the right solution for your business or personal needs.
FAQ
While encryption can make it difficult for hackers to access data, it is not foolproof. Skilled hackers can use various techniques to bypass encryption and access data.
Encryption can slow down the AV solution, especially if the encryption algorithm is complex. However, modern encryption protocols are designed to be fast and efficient.
No, asymmetric encryption is more secure than symmetric encryption because it uses two different keys.
No, encryption cannot protect against all cyberattacks. It is just one of the many security measures that should be implemented to protect against cyber threats.
Yes, encryption can be applied to all types of data, including user credentials, virus definitions, and updates.
Others also read the following article
Want to know more about the Audio Visual Solutions?
